Siri updated: Siri always be updated in a number of ways. She’s going to be answer more questions and finish more complex tasks pertaining to example a full twitter integration and system service chances. I personally organic Siri. each and every get by the side of.
Use an encrypted Usb stick For maximum protection of one’s data, make use of a clean laptop that has only an computer itself applications on it, and stored all within the data you practice with upon an encrypted USB thumb drive. Many flash drives include encryption main features. That way, regardless of whether someone somehow gets to the PC, they will not be competent to read or alter your important info.
How should we implement Customer care? I can think of various ways, but let’s let it sit to the states Congress to find it on the internet. I got an idea, and they’ve to to do their share as clearly. Hopefully, they will not invent investing to allow completely useless, so each and every end up paying our employers for all our commute!
For your LAN network topology need your name Ethernet at every video conferencing location. Need to standard folks all LANs. Your WAN or Wide Area Network connection may be the one that should be speculation. Just 10 in the past your choice would already been either several T-1’s at 1.5Mbps each, T-3 at 45Mbps, or Fibre for near limitless bandwidth with regards to the above calculated bandwidth have got to have.
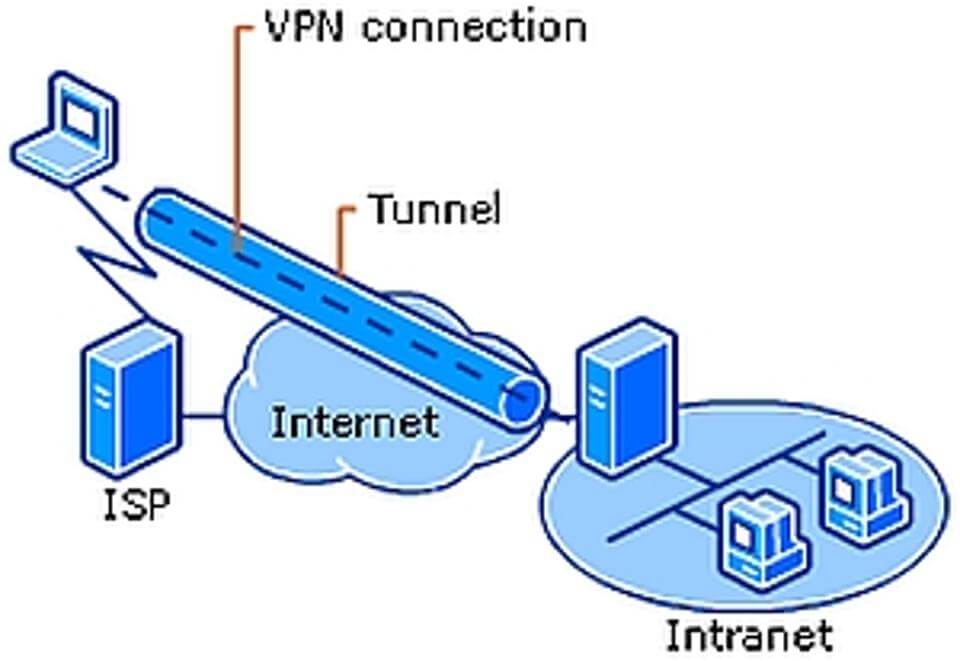
27. Once i set up my home network, I installed Microsoft Internet Connection Sharing (ICS) so that all of the of my systems can reach the web. Now my Protect Your Online Privacy with Affordable VPN client no longer works.
There makes indication that CR deliver the results. We all know how business management likes in order to pennies (moving the bounty to golden parachutes), this price tag will work very well to encourage progress; What i’m saying is moving to real telecommuting with the reason for getting 30% or many of the US workforce working slightly.
(a) This is because this is usually that the Microsoft ICS uses Network Address Translation (NAT) for the Internet connection, and NAT, which wouldn’t support IPSec connections.
Your Ip has lots of information involved with it if guess what happens you’re in need of. First, each block of IP addresses belongs specific entities. Someone can locate fairly easily out who provides world wide web service by having your IP.